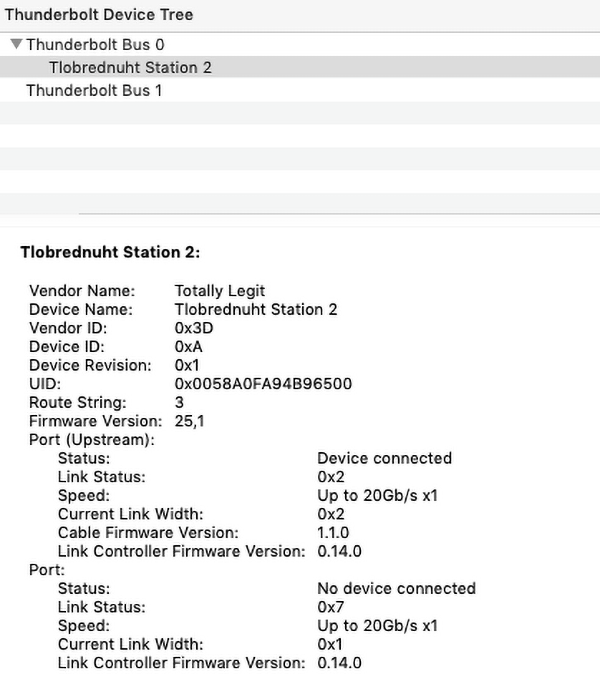
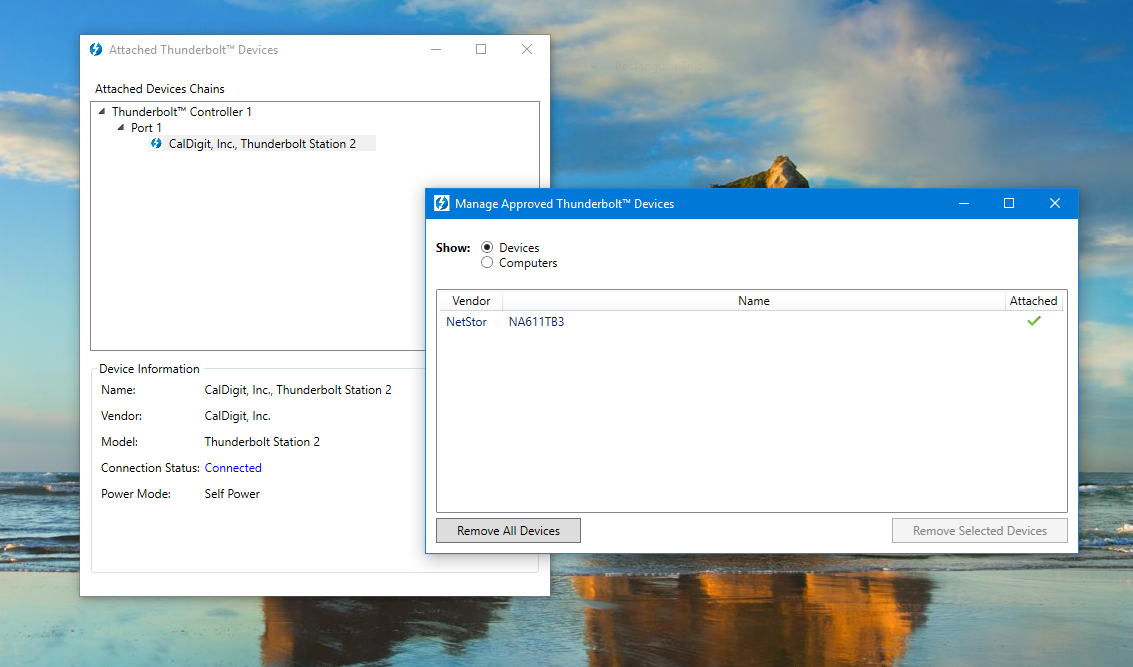
Thunderspy targets devices with a Thunderbolt port. If your computer has such a port, an attacker who gets brief physical access to it can read and copy all your data, even if your drive is encrypted and your computer is locked or set to sleep.
Thunderspy is stealth, meaning that you cannot find any traces of the attack. It does not require your involvement, i.e., there is no phishing link or malicious piece of hardware that the attacker tricks you into using. Thunderspy works even if you follow best security practices by locking or suspending your computer when leaving briefly, and if your system administrator has set up the device with Secure Boot, strong BIOS and operating system account passwords, and enabled full disk encryption. All the attacker needs is 5 minutes alone with the computer, a screwdriver, and some easily portable hardware.
We have found 7 vulnerabilities in Intel’s design and developed 9 realistic scenarios how these could be exploited by a malicious entity to get access to your system, past the defenses that Intel had set up for your protection.
We have developed a free and open-source tool, Spycheck, to determine if your system is vulnerable. If it is found to be vulnerable, Spycheck will guide you to recommendations on how to help protect your system.
Update June 24, 2021
Today, we are happy to announce MITRE released CAPEC
version 3.5, adding Thunderspy under the attack pattern CAPEC-665: Exploitation of Thunderbolt
Protection Flaws.
Update 29 Dec, 2020
Our Chaos Communication Congress (rC3) talk is online here: live recording and slides.
Update 14 Aug, 2020
Our Black Hat USA talk is online here: live
recording and slides.
Update 6 Aug, 2020
Today, we are happy to release two tools to patch your system to achieve the same (partial) security that
Intel's
Kernel DMA Protection offers against Thunderspy. These tools aim to
bring Kernel DMA
Protection to all systems released between 2013 and 2020 that do not ship Kernel DMA Protection, but are
in fact technically capable. Please visit our Thunderspy 2 page for more
details. The same fix could be provided systematically by vendors if they update their UEFI (BIOS)
distributions.
Thunderspy PoCs in Action
Cloning user-authorized device identities to arbitrary attacker devices
Thunderspy enables creating arbitrary Thunderbolt device identities and cloning user-authorized Thunderbolt devices, even in the presence of Security Levels pre-boot protection and cryptographic device authentication.
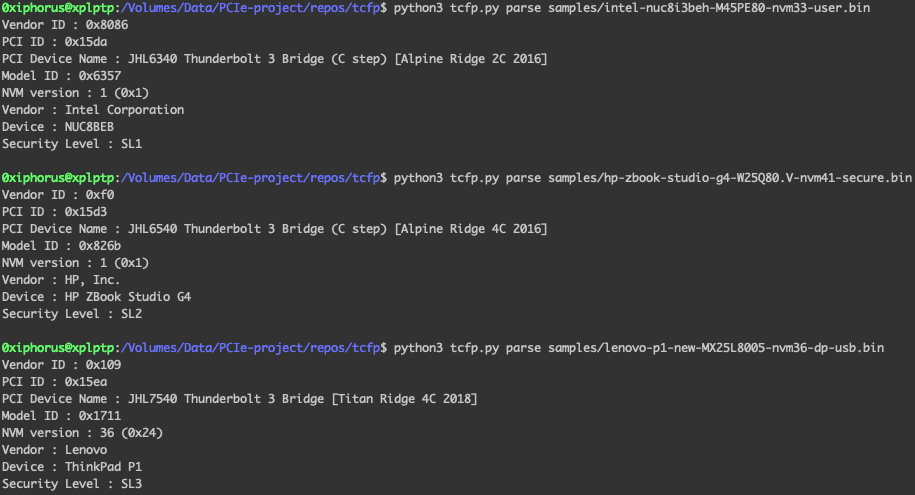
Permanently disabling Thunderbolt security and future firmware updates
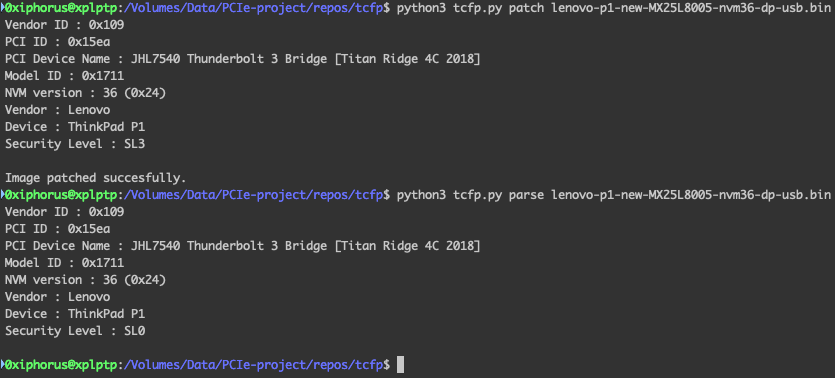
Thunderbolt Controller Firmware Patcher (tcfp), a firmware patching toolkit we have developed, enables disabling Thunderbolt security without requiring access to the victim system BIOS or OS. Moreover, tcfp enables disabling Thunderbolt security covertly - without reflecting the new state in the BIOS.
SPIblock, another tool we have developed, allows programming on-flash write protection. Specifically, this includes configuring SPI flash to employ an irrevocable, read-only state. When combined with tcfp, it allows to permanently, and covertly, disable Thunderbolt security and block all future firmware updates.
Full Summary
Thunderbolt is a high-bandwidth interconnect promoted by Intel and included in laptops, desktops, and other systems. Being PCIe-based, Thunderbolt devices possess Direct Memory Access (DMA)-enabled I/O. In an evil maid DMA attack, where adversaries obtain brief physical access to the victim system, Thunderbolt has been shown to be a viable entry point in stealing data from encrypted drives and reading and writing all of system memory. In response, Intel introduced Security Levels, a security architecture designed to enable users to authorize trusted Thunderbolt devices only. To further strengthen device authentication, the system is said to provide “cryptographic authentication of connections” to prevent devices from spoofing user-authorized devices.
We present Thunderspy, a series of attacks that break all primary security
claims for Thunderbolt 1, 2,
and 3. So far, our research has found the following vulnerabilities:
- Inadequate firmware verification schemes
- Weak device authentication scheme
- Use of unauthenticated device metadata
- Downgrade attack using backwards compatibility
- Use of unauthenticated controller configurations
- SPI flash interface deficiencies
- No Thunderbolt security on Boot Camp
All Thunderbolt-equipped systems shipped between 2011-2020 are vulnerable. Some systems providing Kernel DMA Protection, shipping since 2019, are partially vulnerable. The Thunderspy vulnerabilities cannot be fixed in software, impact future standards such as USB 4 and Thunderbolt 4, and will require a silicon redesign. Users are therefore strongly encouraged to determine whether they are affected using Spycheck, a free and open-source tool we have developed that verifies whether their systems are vulnerable to Thunderspy. If it is found to be vulnerable, Spycheck will guide users to recommendations on how to help protect their system.
Thunderbolt: A Closer Look
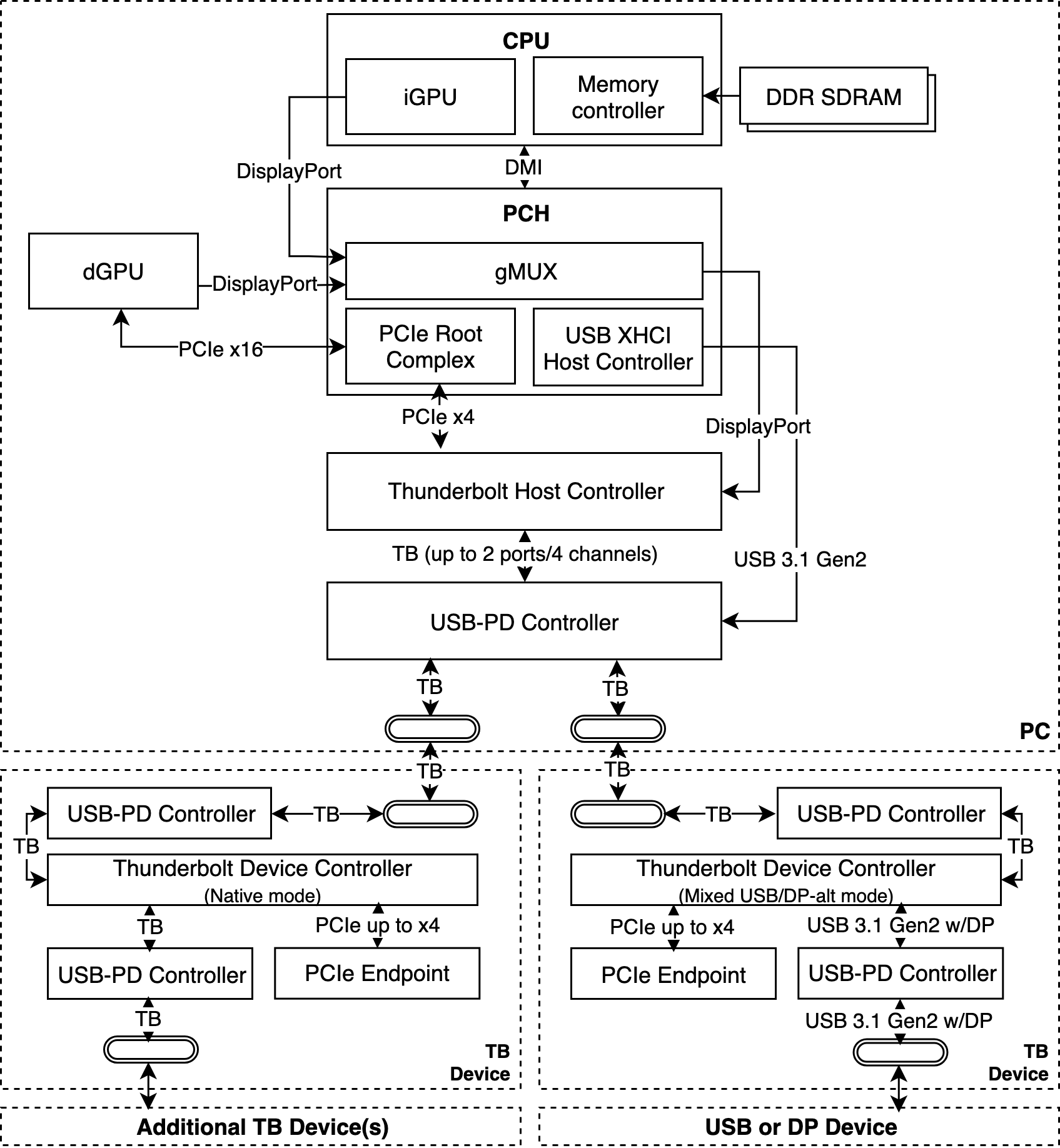
Thunderbolt controllers can operate in either Host Mode or Endpoint Mode. In Host Mode, Thunderbolt controllers connect to the system using a bare-metal PCIe interface. Pictured is an example PCIe topology in more detail. As can be seen, in this situation, the PCH exposes a PCIe x4 link to a Thunderbolt 3 controller. USB support is implemented using two auxiliary components. While the PCH provides a USB 3.1-compliant host controller, a third-party IC extends USB signaling with Power Delivery support, and concurrently multiplexes between Thunderbolt and USB signaling as appropriate. To this end, Thunderbolt 3 defines silicon that can dynamically switch between the following PHY modes:
- USB passthrough mode. If a USB device is plugged in, the PCH USB host controller is activated. In this mode, the Thunderbolt 3 port operates as a USB 3.0 Type C interface, that is, without DisplayPort (DP) alt-mode support.
- Mixed USB/DisplayPort mode. Enables support for “mixed mode” devices, such as USB Type C hubs with DisplayPort sinks. In this mode, the Thunderbolt 3 port operates as a USB 3.1 Gen 2 Type C interface supporting DP alt-mode.
- Native Thunderbolt mode. If a Thunderbolt device is plugged in, the Thunderbolt silicon enables two full-duplex links to the device providing a per-link throughput between 10 to 20 Gbps, depending on the negotiated Thunderbolt version. The device, operating in Endpoint Mode, demultiplexes these links to a maximum of four PCI Express lanes and two four-lane DP streams.
Thunderbolt devices can be daisy-chained. Aside from sharing one port between multiple devices, daisy-chaining allows for a variety of topologies with mixed controller configurations, such as illustrated in in the figure. Contrary to USB, Thunderbolt is a proprietary connectivity standard. Device vendors are required to apply for Intel’s Thunderbolt developer program, in order to obtain access to protocol specifications and the Thunderbolt hardware supply chain. In addition, devices are subject to certification procedures before being admitted to the Thunderbolt ecosystem.
Thunderbolt controller hardware architecture experimentally derived during our
study
(Image by Björn Ruytenberg. Licensed under CC BY
4.0.)
Who discovered Thunderspy?
The Thunderspy vulnerabilities have been discovered and reported by Björn Ruytenberg. Please cite this work as:
Björn Ruytenberg. Breaking Thunderbolt Protocol
Security:
Vulnerability Report. 2020.
https://thunderspy.io/assets/reports/breaking-thunderbolt-security-bjorn-ruytenberg-20200417.pdf
Disclosure Timeline
We disclosed vulnerabilities 1-5 to Intel on February 10, 2020. They wrote on March 10, 2020 that their engineering team confirmed the vulnerabilities, and that vulnerabilities 3-5 were new to them. After further research we disclosed vulnerability 6, which Intel confirmed on March 17, 2020.
In our first email we asked Intel to promptly notify affected parties, in coordination with us. However, Intel did not take any action and finally, after several email exchanges, listed only 5 parties whom they would inform. We then sent them a list of other parties we had identified as affected, including 11 OEMs/ODMs and the Linux kernel security team. Eventually they notified us that they informed some parties on 25 March, 2020 about the vulnerabilities and upcoming disclosure, without giving us details of what this information consisted of and whom exactly they contacted. We reached out to several more parties after realizing that they had been skipped by Intel.
Finally, we informed Apple of vulnerability 7 on April 17, 2020.
Questions and Answers
I have a laptop or desktop PC running Windows. Am I affected?
To determine whether your system is vulnerable to Thunderspy, we strongly recommend to run our verification tool Spycheck. Alternatively, you can also verify your system manually. Running Windows on a Mac (Boot Camp)? Please refer to affected Apple systems.
Verifying using Spycheck
- Download and extract the Spycheck ZIP to a folder of your choice. For example, on your Windows desktop, create a new folder named "Spycheck".
- In the "Spycheck" folder, double-click on the Spycheck icon. At this point, Windows SmartScreen may warn you the program has not been signed and is therefore untrusted. Please confirm you wish to run it.
- After selecting a language and accepting the open-source GPLv3 license, you will be asked to confirm your system has Thunderbolt ports.
- At this point, Spycheck will try to detect your system's Thunderbolt controller.
On some systems, the controller might enter a power saving mode when no Thunderbolt devices are connected. If this is the case with your laptop, please connect a Thunderbolt device to power up the controller. Alternatively, if you don't have any Thunderbolt devices to connect, Spycheck bundles a custom power management driver to enable power to the controller. If you choose to install this driver, please note you may be warned again by Windows SmartScreen. After installing the driver, you may be asked to restart Windows, after which you should run Spycheck again. - Finally, Spycheck will show you an analysis summary. A more detailed report is available by clicking on the "Report" button in the summary screen. If you wish, you can then export the report to JSON, or copy the report text to another program of your choice.
Verifying manually
- Please identify the ports on your system:

(i). USB-C or Mini-DisplayPort with lightning symbol

(ii). USB-C or Mini-DisplayPort without lightning symbol
If your system provides any ports as pictured in (i), it features Thunderbolt connectivity, and is therefore vulnerable to Thunderspy. Please proceed to the next step. Otherwise, if your system does not provide any ports as pictured in (i), or these look similar to the ports pictured in (ii), then it is not vulnerable to Thunderspy.
- Systems purchased before 2019:
No fix is available. For recommendations on how to help protect your system, please refer to protections against Thunderspy.Systems purchased in or after 2019:
Your system might support Kernel DMA Protection, which partially mitigates Thunderspy. For instructions on how to verify whether your system ships this protection, please refer to Kernel DMA Protection.
I have a laptop or desktop PC running Linux. Am I affected?
To determine whether your system is vulnerable to Thunderspy, we strongly recommend to run our verification tool Spycheck. Alternatively, you can also verify your system manually. Running Linux on a Mac (Boot Camp)? Please refer to affected Apple systems.
Verifying using Spycheck
- While Spycheck supports running without root privileges, it requires root
to
generate an
accurate
report. To verify whether your system is vulnerable to Thunderspy, simply download
and run the script as follows 1:
$ sudo python3 spycheck.py
When running Spycheck, you will be asked to identify the ports on your system. If you indicate your system provides Thunderbolt ports, the tool will attempt to detect Thunderbolt hardware and assess whether your system is vulnerable to Thunderspy.
1 To run without root, omit "sudo" from the command line above.
- Finally, Spycheck will show you a detailed report. If you wish, you can export the report to JSON by passing "-o FILE.json".
Verifying manually
- Please identify the ports on your system:

(i). USB-C or Mini-DisplayPort with lightning symbol

(ii). USB-C or Mini-DisplayPort without lightning symbol
If your system provides any ports as pictured in (i), it features Thunderbolt connectivity, and is therefore vulnerable to Thunderspy. Please proceed to the next step. Otherwise, if your system does not provide any ports as pictured in (i), or these look similar to the ports pictured in (ii), then it is not vulnerable to Thunderspy. - Systems purchased before 2019:
No fix is available. For recommendations on how to help protect your system, please refer to protections against Thunderspy.Systems purchased in or after 2019:
Your system might support Kernel DMA Protection, which partially mitigates Thunderspy. For instructions on how to verify whether your system ships this protection, please refer to Kernel DMA Protection.
I have an Apple Mac. Am I affected?
All Apple Macs released from 2011 onward, except for Retina MacBooks, provide Thunderbolt connectivity and are therefore vulnerable to Thunderspy. You may wish to learn more about Thunderbolt-equipped Macs on Apple's website. For more information on Apple's position regarding Thunderspy, please refer to why has Apple not fixed Thunderspy.
MacOS
If you are running MacOS, your system is partially affected by Thunderspy. For recommendations on how to help protect your system, please refer to protections against Thunderspy.
Windows and Linux (Boot Camp)
When running any OS other than MacOS, Apple Macs disable all Thunderbolt security. Hence, if you are running Windows or Linux using the Boot Camp utility, your system is fully affected by Thunderspy.
I have an affected system. How can I protect myself?
- Connect only your own Thunderbolt peripherals. Never lend them to anybody.
- Avoid leaving your system unattended while powered on, even when screenlocked.
- Avoid leaving your Thunderbolt peripherals unattended.
- Ensure appropriate physical security when storing your system and any Thunderbolt devices, including Thunderbolt-powered displays.
- Consider using hibernation (Suspend-to-Disk) or powering off the system completely. Specifically, avoid using sleep mode (Suspend-to-RAM).
- Disable the Thunderbolt controller entirely in UEFI (BIOS). Please note that this renders all Thunderbolt ports inoperable, including USB and DisplayPort connectivity. However, USB-C charging will most likely remain functioning.
I have configured Thunderbolt to pass through USB/DisplayPort only. Am I protected?
What is Kernel DMA Protection?
Kernel DMA Protection is Intel's implementation of DMA remapping for Thunderbolt devices. When enabled on supported systems, this protection scheme aims to restrict all Thunderbolt devices to IOMMU-controlled memory ranges. Kernel DMA Protection mitigates some, but not all of the Thunderspy vulnerabilities. While it prevents any further impact on victim system security via DMA, the remaining Thunderspy vulnerabilities expose the system to attacks similar to BadUSB.
If you do not intend to use Thunderbolt, we recommend to disable Thunderbolt in UEFI (BIOS). Otherwise, please proceed below.
Thunderbolt device compatibility
Please note that enabling Kernel DMA Protection is known to cause compatibility issues with a number of Thunderbolt peripherals.
Supported systems
Kernel DMA Protection requires hardware and UEFI (BIOS) support, and is therefore only available on compatible systems shipping from 2019 onward. Hence, all systems released before 2019, and more recent systems that do not ship Kernel DMA Protection, will remain fully vulnerable to Thunderspy forever. If your system does not provide this protection scheme, please refer to protections against Thunderspy instead. You can learn more about Kernel DMA Protection on Microsoft's website.
Verifying whether your system supports Kernel DMA Protection
If you have purchased your Thunderbolt system in or after 2019, it might ship Kernel DMA Protection. Currently, we are aware of support on a limited number of models. Owners of these models may verify support as follows:
- HP EliteBook and ZBook (2019 and later): Power on the system and press F2. In the "Startup Menu" screen, select "BIOS setup (F10)". From the "Advanced" menu, select "System Options". In the screen that follows, verify "DMA Protection" is enabled.
- Lenovo ThinkPad P53, X1 Carbon (2019 and later): Power on the system and press F1. From the "Security" tab, select "Virtualization". In the screen that follows, verify "Kernel DMA Protection" is enabled.
- Lenovo Yoga C940 (models with Ice Lake CPU only): Always enabled by default. Status cannot be queried from UEFI.
- Thunderbolt 4-certified systems: Currently, these include Intel laptop systems equipped with a Tiger Lake or Alder Lake CPU, and Rocket Lake desktops when paired with a Thunderbolt 4 host controller. Please refer to Is Thunderbolt 4 affected? for more information.
If Spycheck reports your system provides Kernel DMA Protection, but does not appear in the former list, please reach out to bjornbjornwebnl using the subject "Thunderspy: new kDMAp system", while attaching Spycheck's JSON report. Thanks!
After enabling Kernel DMA Protection, my Thunderbolt devices stopped working. What happened?
Thunderspy variants 5 and 6 allow permanently disabling security and blocking firmware updates. How can I tell whether I have been attacked?
In our study, we have found Thunderbolt controllers lack handling hardware error conditions when interacting with flash devices. Specifically, we have determined enabling flash write protection (i) prevents changing the Security Level configuration in UEFI, without being reflected in the latter, and (ii) prevents controller firmware from being updated, without such failures being reflected in Thunderbolt firmware update applications. As such, when combined with the fifth issue, this vulnerability allows to covertly, and permanently, disable Thunderbolt security and block all future firmware updates.
Please note that while verification is a straightforward procedure, recovering from this attack may require significant technical expertise, or may not be possible at all. For more information, please refer to our vulnerability report.
Verifying whether you are victim of Thunderspy attack variants 5 and 6
- In UEFI (BIOS), modify the Thunderbolt Security Level to any value other than "None" (SL0); for example, choose "Secure" (SL2).
- Reboot to UEFI, and verify the Thunderbolt Security Level is set to the desired value.
- Continue booting to the OS, and connect any Thunderbolt device.
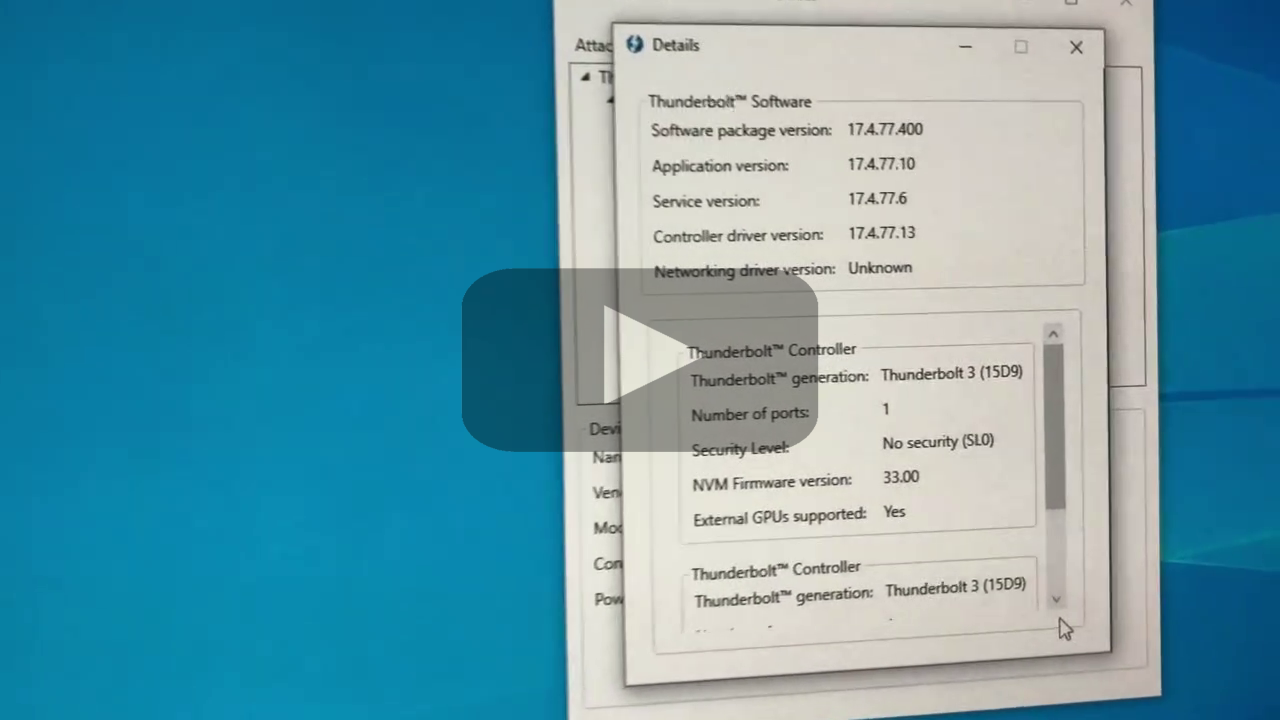
- If you are running Windows, navigate to the "About" section of the Thunderbolt Software application,
and record the currently active Security Level.
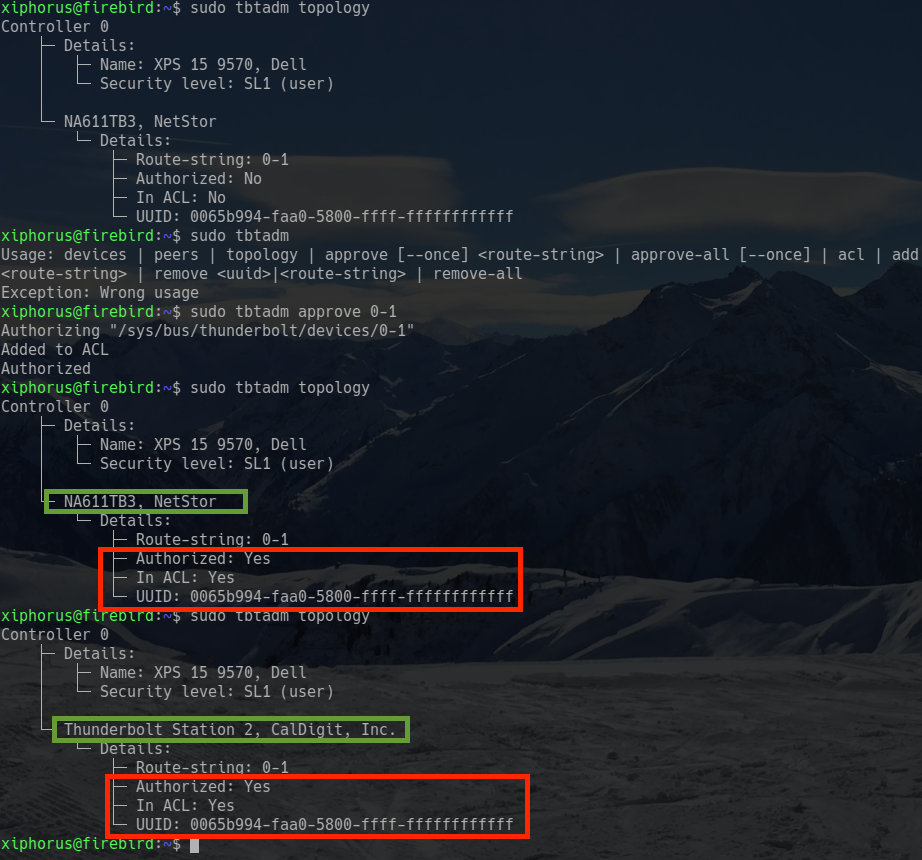
If you are running Linux, record the currently active Security Level by running:
$ sudo tbtadm topology
In both cases, verify that the currently active Security Level matches the value set in the first step. If it does not match, then your system has become victim to an attacker abusing Thunderspy variants 5 and 6.
Recovering from Thunderspy attack variants 5 and 6
Depending on the exploitation method, recovering from this attack may require significant technical expertise, or may not be possible at all. In carrying out the following instructions, please consult a person with an appropriate technical background. Incorrectly applying any of these instructions may damage your system and/or void its warranty.
- Soft-block method: (i) Using SPIblock, disable block protection on the Thunderbolt controller SPI flash. (ii) Refer to protections against Thunderspy for recommendations on how to help protect your system.
- Hard-block method: (i) Inspect the Thunderbolt controller SPI flash, and desolder any wires from the GND to WP pins. No wires should be visible if the attacker has not used this method. (ii) Using SPIblock, disable write and block protection on the Thunderbolt controller SPI flash. (iii) Refer to protections against Thunderspy for recommendations on how to help protect your system.
- One Time Program method: The SPI flash storing the Thunderbolt controller firmware has been set to an irrevocable read-only state. Therefore, Thunderbolt security will be permanently disabled on your system. No recovery is possible.
Why has Intel not fixed Thunderspy?
- All three versions of Thunderbolt are affected by the Thunderspy vulnerabilities.
- Only systems shipping Kernel DMA Protection mitigate some, not all, of the Thunderspy vulnerabilities.
- Only some systems that began shipping since 2019 come with Kernel DMA Protection.
- Beyond Kernel DMA Protection, Intel will not provide any mitigations to address the Thunderspy vulnerabilities. Hence, Intel will not assign any CVEs to the Thunderspy vulnerabilities, or release any public security advisories to inform the general public.
Despite our repeated efforts, the rationale to Intel's decision not to mitigate the Thunderspy vulnerabilities on in-market systems remains unknown. Given the nature of Thunderspy, however, we believe it would be reasonable to assume these cannot be fixed and require a silicon redesign. Indeed, for future systems implementing Thunderbolt technology, Intel has stated they will incorporate additional hardware protections.
Kernel DMA Protection is only available on a limited number of recent systems. Hence, all systems released before 2019, and more recent systems that do not ship Kernel DMA Protection, will remain fully vulnerable to Thunderspy forever. Please refer to Kernel DMA Protection for more information.
Why has Apple not fixed Thunderspy?
In our vulnerability disclosure procedure, Apple has stated the following:
"Some of the hardware security features you outlined are only available when users run macOS. If users are concerned about any of the issues in your paper, we recommend that they use macOS."
To verify whether your system is affected by Thunderspy, please refer to affected Apple Mac systems.
Intel has stated they had been already aware of Thunderspy variants 1 and 2. Why haven't they disclosed these issues before?
In our vulnerability disclosure procedure, Intel has not shared why they have chosen not to inform the general public of these issues before. Please refer to the previous question for more information on Intel's position.
How can I distinguish Thunderbolt devices from USB-C devices?
Suppose I inadvertently connect a malicious Thunderbolt device masquerading as USB-C. How can I prevent it from compromising my system?
In the context of evil maid and supply chain attacks, devices may physically appear to implement USB-C - for example, by its connector not carrying any lightning symbols - while internally hardware may have been tampered with to incorporate a malicious Thunderbolt device instead. This may apply particularly to seemingly innocuous peripherals such as USB-C to DisplayPort/HDMI dongles. To help protect your system against such attacks, consider connecting these devices exclusively using one of the following:
- USB-C female to USB-A male dongles. Connect the device to a USB-A ("regular" USB) port. Optionally, connect the former dongle to a USB-A female to USB-C male dongle, and finally connect the entire chain to a Thunderbolt 3 port. Please note that, if supported by the device, this setup may reduce performance from USB 3.1 Gen 2 (10 Gbps) to USB 3.1 Gen 1 (5 Gbps) speeds, and prevent DP/HDMI signaling.
- USB-C extension cables certified for USB 2.0 or 3.1 Gen 1 speeds. Please note that this setup may reduce performance accordingly. However, DP/HDMI will most likely remain functioning.
Please note: while product descriptions may suggest otherwise, non-Thunderbolt USB-C cables are usually also capable of carrying Thunderbolt signaling. We therefore strongly recommend to avoid cables certified for the following standards:
- USB 3.1 Gen 2 (10 Gbps)
- USB 3.2 Gen 2 (10 Gbps)
- USB 3.2 Gen 2x2 (20 Gbps)
Is USB-C affected?
USB 4 is based on Thunderbolt 3. Is this interface affected as well?
Is Thunderbolt 4 affected?
Update 26 January 2021
Starting with Thunderbolt 4, Intel's
Thunderbolt certification program requires vendors to
implement Kernel DMA Protection. As opposed to Thunderbolt 3, where all systems released before 2019 and
various since 2019 will remain fully
vulnerable to Thunderspy forever, essentially this means Thunderbolt 4 systems
will be the first generation to warrant Kernel DMA Protection support. However, we
would like to
emphasize Kernel DMA Protection only partially mitigates Thunderspy. Please
refer to What is Kernel
DMA Protection? for more
information.
How does Thunderspy augment previous work, such as PCILeech and Thunderclap?
Previous studies have primarily focused on employing DMA and IOMMU attacks on the PCIe level to compromise Thunderbolt security. Maartmann-Moe (Inception), Frisk (PCILeech) and others have shown Thunderbolt 1 to be a viable entry point in stealing data from encrypted drives and reading and writing all of system memory.
In response, Intel introduced "Security Levels" with Thunderbolt 2, a security architecture designed to protect against all former attacks by enabling users to authorize trusted Thunderbolt devices only. To further strengthen device authentication, the system is said to provide "cryptographic authentication of connections" to prevent devices from spoofing user-authorized devices.
More recent attacks like Thunderclap (Markettos, Rothwell, Gutstein, Pearce, Neumann, Moore, Watson) work within the "Security Levels" ecosystem to attack the IOMMU and do not break Thunderbolt access control. They instead rely on tricking the user into accepting a malicious device as a trusted one. Once enabled, such a device can do a DMA attack similar to without Security Levels.
Our research goes beyond where the current state of the art has ended, by breaking Thunderbolt hardware and protocol security. This is the first attack on Intel's Security Levels. In addition, Intel's response to Thunderclap stated "Existing security options for the Thunderbolt interface also allow you to whitelist trusted Thunderbolt devices to help protect your systems from malicious peripherals" as a remedy to Thunderclap. Our attack, Thunderspy, completely breaks these security options.
Finally, the scope of our work demonstrates how issues residing in one domain (hardware, firmware or software) may lead to compromising security in the other domains.
The full summary mentions this disclosure is part of on-going research. Will there be more?
Stay tuned for Thunderspy 2: Judgment Day.
Update 6 Aug 2020
Today, we are happy to release two tools to patch your system to achieve the same (partial) security that
Intel's
Kernel DMA Protection offers against Thunderspy. These tools aim to
bring Kernel DMA
Protection to all systems released between 2013 and 2020 that do not ship Kernel DMA Protection, but are
in fact technically capable. Please visit our Thunderspy 2 page for more
details. The same fix could be provided systematically by vendors if they update their UEFI (BIOS)
distributions.
Why is it called Thunderspy?
Can I use the logo?
Thunderspy in the Media
Jump to: Press Coverage • Security AdvisoriesPress Coverage
10 May 2020, WIRED, "Thunderbolt Flaws Expose Millions of PCs to Hands-On Hacking"
11 May 2020, Eindhoven University of Technology, "Eindhoven security researchers find fatal vulnerabilities in Thunderbolt"
11 May 2020, Engadget, "Thunderbolt flaw lets hackers steal your data in 'five minutes'"
11 May 2020, The Verge, "Thunderbolt flaw allows access to a PC's data in minutes"
11 May 2020, ZDNet, "Thunderbolt flaws affect millions of computers - even locking unattended devices won't help"
11 May 2020, TechPowerUp, "Unfixable Flaw Found in Thunderbolt Port that Unlocks any PC in Less Than 5 Minutes"
11 May 2020, Decipher, "Thunderspy Attack Underscores Existing Thunderbolt Security Issues"
11 May 2020, Mashable, "Thunderbolt bugs can expose your PC if you leave it alone with a hacker"
11 May 2020, Tweakers, "Eindhovense onderzoeker kraakt Thunderbolt 3-beveiliging"
11 May 2020, NOS, "Nederlandse onderzoeker vindt lek in aansluiting computers"
11 May 2020, RTL Nieuws, "'Thunderbolt-poorten in miljoenen apparaten kwetsbaar'"
11 May 2020, Eindhovens Dagblad, "TU/e-student ontdekt beveiligingslek in veelgebruikte verbinding"
11 May 2020, Hardware.info, "Beveiliging Thunderbolt opnieuw gekraakt"
11 May 2020, Security.nl, "Thunderbolt-lek geeft fysieke aanvaller toegang tot vergrendelde pc"
11 May 2020, Heise, "Thunderspy: Notebooks über Thunderbolt-Anschluss kapern"
11 May 2020, Computerbase, "Thunderspy: Sicherheitslücken in allen Thunderbolt-Generationen"
11 May 2020, PCMag, "Thunderbolt Flaw Allows Your Data to Be Stolen in 5 Minutes"
11 May 2020, The Independent, "Major computer bug means millions could be at risk of hack, security expert warns"
11 May 2020, Phoronix, "Thunderspy Is A New Vulnerability Affecting Thunderbolt Security"
11 May 2020, AppleInsider, "Macs 'partially affected' by unpatchable Thunderbolt security exploit"
11 May 2020, Gizmodo, "A New Flaw Means You Can’t Let Your Thunderbolt Laptop Out of Your Sight"
11 May 2020, Bleeping Computer, "New Thunderbolt security flaws affect systems shipped before 2019"
11 May 2020, SecurityWeek, "Thunderspy: More Thunderbolt Flaws Expose Millions of Computers to Attacks"
11 May 2020, SC Magazine, "Thunderbolt ports vulnerable to hands-on hacks"
12 May 2020, Ars Technica, "Thunderspy: What it is, why it’s not scary, and what to do about it"
12 May 2020, ESET, "Thunderbolt flaws open millions of PCs to physical hacking"
12 May 2020, Sophos, "Thunderspy – why turning your computer off is a cool idea!"
12 May 2020, The Independent, "Thunderspy attack: How to protect your Mac, Windows or Linux computer from hackers"
12 May 2020, MacWorld, "How to protect your Mac from the Thunderbolt security flaw"
12 May 2020, Schneier on Security, "Attack Against PC Thunderbolt Port"
12 May 2020, Security Now!, "Episode 766 - Thunderspy"
13 May 2020, CNN, "This security flaw puts millions of computers at risk for a serious (but unlikely) hack"
13 May 2020, StorageReview, "Heads Up! Thunderbolt Flaws Revealed: Thunderspy"
14 May 2020, ZDNet, "Microsoft: Worried about Thunderbolt attacks? Get a Windows 10 Secured-Core PC"
14 May 2020, Windows Central, "Microsoft explains how secured-core PCs mitigate Thunderspy and other attacks"
17 May 2020, Forbes, "Microsoft Confirms Serious New Security Problem For Windows 10 Users"
21 May 2020, Computerworld, "Dutch security researcher exposes Thunderbolt flaw in most pre-2019 PCs"
8 July 2020, 9to5Mac, "Thunderbolt 4 won't be faster than Thunderbolt 3, but will be better – Intel"
17 July 2020, Engadget, "What Intel's Thunderbolt 4 means for your next PC"
26 January 2021, PCMag, "What Is Thunderbolt 4? Why This New Interface Will Matter in PCs in 2021"
27 February 2021, Tweakers, "Tien jaar Thunderbolt - Van eigen interface naar integratie in USB4"
Security Advisories
11 May 2020, NCSC, "NCSC-2020-0377: Thunderspy kwetsbaarheden in Thunderbolt"
13 May 2020, Microsoft, "Secured-core PCs help customers stay ahead of advanced data theft"
13 May 2020, TWCERT/CC, "Thunderbolt 界面遭發現多個資安漏洞,可讓駭侵者直接連上電腦系統 PCIe 匯流排並發動攻擊"
21 April 2021, MITRE Corporation, "Addressing Thunderspy, One Weakness at A Time"
24 June 2021, MITRE Corporation, "CAPEC-665: Exploitation of Thunderbolt Protection Flaws"

 Spycheck for Windows
Spycheck for Windows Spycheck for
Linux
Spycheck for
Linux